PARTsolutions supports several user databases. One or more of them can be active at a given time. However, only Windows allows for automatic login within the clients. In all other cases, the manual input of the password is mandatory at login time.
In order for Users/Groups to be displayed on the tabbed page Assign rights, on the corresponding tabbed pages, set a checkmark under Active. The sequence of evaluation is according to the sequence of tabs: Windows, then ERP, then the others...
Limit for queries: Max value is 999999.
Limitation can be helpful, on the other hand it can lead to incomplete results.
At the latest a number of more than 9999 entries in AD definitely causes that the search function under Assign rights -> Known users/groups will not work properly, possibly even before, however, this can be compensated by using the button.
In general the behavior strongly depends on the concrete AD server.
SSO configuration with Microsoft Azure
Note: OpenID does not work in batch processes (that's why also Windows has to be activated under User databases).
In the following you can find a detailed description, which has just to be modified for your own environment.
In the first step add an APP registration for CADENAS PARTsolutions/3DFindIt in your company in Microsoft Azure.
Call https://portal.azure.com.
Pick an account in Microsoft Azure.
Fill out the dialog Register an application and finally click on .
Name: Enter any display name (e.g. "CADENAS PARTsolutions/3DFindIt").
Supported account types: Select the option Accounts in this organizational directory only (<your company> only - Single tenant) (in the exemplary figure "CADENAS Technologies AG"),
Redirect URI (optional): In the list field, select Public client/native (mobile & desktop) and in the input field, enter http://localhost/auth/login.
Filter for the just registered application.
Select item Token configuration and click on Add groups claim.
Fill out the dialog page Edit groups claim in the following way:
Open the Essentials. Here, you can copy the desired IDs into the clipboard in order to insert them in PARTadmin.
In PARTadmin, under category Rights administration, select the tabbed page User databases and the subpage OpenID.
Under Basic Type, select the option Microsoft Azure AD.
Fill out the individual fields according to the data from Microsoft Azure:
Issuer: This url specifies the path to the Openid provider realm or Azure tenant.
https://login.microsoftonline.com/<Tenant-ID>/
Client-ID/App-ID: The application ID or client ID for PARTsolutions in the OpenId provider (AppId in the application registration of the Azure portal)
Client-Secret: The client secret that is stored in the app registration for this client. Can be omitted if there is no need to list the users/groups via the Graph API. Is only relevant for Azure.
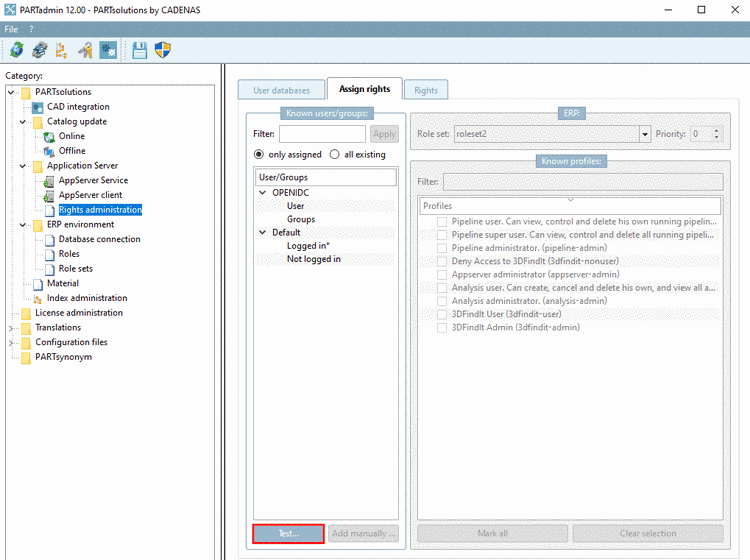
The desired group can also be added manually when using Test... in order to detect the correct group name.
Normally this option is not absolutely required except when using the option Identify additional attributes using the UserInfo endpoint.
Under Certificates & secrets you can create and read IDs.
Scopes: Required scopes for authentication. Separated by spaces. The default is "openid offline_access"
Username-Claims (optional): Comma-separated list of claims to be considered as the source for the user ID. The default setting here is "preferred_username,upn,email,sub"
Group Claim (optional): Name of the claim from which the group membership is to be extracted. The default is "groups" for Azure and "roles" for everything else. Can be switched to any other claim here.
Required group: Name of a group in which the user must be in order to be considered a valid user. If no entry is specified, all users are considered valid.
Identify additional attributes using the UserInfo endpoint: Not relevant for Azure.
Open PARTadmin -> category Rights administration -> tabbed page Assign rights.
-> The dialog box Check authentification... is opened.
Select the option OPENID and click Login....
-> The dialog box Authenticate user is opened.
Pick your account, enter your password and click .
-> In the dialog area Result, the data is displayed.
Select the item User or Groups and click .
-> The dialog box Enter group... is opened.
Assign the desired role set to group or user.
For testing, start PARTdataManager and click on the button Authenticate/switch users.
-> The dialog Authenticate user is opened.
If a login via Windows user should be possible (autologin), on the tabbed page Windows, the option Active needs to be activated.
By default, the option Active is activated, what makes sense in most cases.
If it becomes deactivated, a Windows-based user authentication is not possible.
Use global catalog for queries: When using an Active Directory Forest activate this option (default is "off")
Limit for queries: Please pay attention that there is no 0 entered here!
This will happen when removing the checkmark Active for Windows, then terminating PARTadmin, then restarting and then activating the user database "Windows" again.
Check for hierarchical group memberships: The check happens recursively through hierarchically superordinated levels.
If problems should occur during auto login in the PARTapplicationServer when using a Windows username, please check the following basic settings:
In the dialog "Internet options" -> tabbed page "Advanced", the option "Enable Integrated Windows Authentication" needs to be enabled.
In the dialog "Security Settings - Local Intranet Zone" the option "Automatic logon only in Intranet zone" has to be enabled.
The http address of the Appserver has to be included in the local Intranet zone.
If a login with ERP users shall be possible in the dialog of user authentication, the option Active has be activated (default).
Create users with the button. In the dialog, set Name and Password. If you want to change the password later (via ), simply set a new one (the old one is not displayed).
If above mentioned preconditions are fulfilled, the user authentication in the dialog Authenticate user can happen by entering user and password.
If there are multiple roles available, the dialog box Select role is opened.
If the user authentication fails, an error message Invalid username or password! is displayed.















![[Note]](https://webapi.partcommunity.com/service/help/latest/pages/cn/partsolutions_user/doc/images/note.png)

![[Tip]](https://webapi.partcommunity.com/service/help/latest/pages/cn/partsolutions_user/doc/images/tip.png)